Contents
Workday and Duo have partnered to offer Duo's MFA authentication as part of Workday's conditional authentication policies.
Overview
Workday's Duo integration supports first-time MFA enrollment and two-factor authentication when logging into Workday from a browser or the Workday mobile app.
At this time you cannot apply the Duo MFA authentication condition to any Workday SSO users federated with an external identity provider. Workday recommends applying two-factor authentication at the SSO IdP. Duo provides multiple options for protecting SSO IdP logins. Please see our Duo Single Sign-On for Workday documentation for more information.
Prerequisites
-
You should have the Duo Owner administrator role. Only admins with the Owner role may create new Admin API applications in the Duo Admin Panel.
-
You should be a Workday administrator with the rights to modify your tenant's security settings and to manage and activate authentication policies.
First Steps
Role required: Owner
- Sign up for a Duo account if you don't already have one, and contact Duo Support to have Admin API enabled for your account.
- Log in to the Duo Admin Panel and navigate to Applications.
- Click Protect an Application and locate the entry for Workday with a protection type of "2FA" in the applications list. Click Protect to the far-right to configure the application and get your integration key, secret key, and API hostname. You'll need this information to complete your setup. See Protecting Applications for more information about protecting applications in Duo and additional application options.
- Click Protect an Application again and locate Admin API in the applications list. Click Protect this Application to get your integration key, secret key, and API hostname. You will need to enter this information into your Workday tenant as well.
- You may find it helpful to give this Admin API application a unique name, like "Workday Admin API".
- While on the new Admin API application's details page, scroll down to the "Permissions" section and enable Grant read information, Grant resource - Read, and Grant resource - Write.
- Click Save Changes.
See Getting Started for help.
The security of your Duo application is tied to the security of your secret key (skey). Secure it as you would any sensitive credential. Don't share it with unauthorized individuals or email it to anyone under any circumstances!
Configure Duo MFA in Workday
-
Log on to your Workday tenant as an administrator and access the Edit Tenant Setup - Security task.
-
Once on the "Edit Tenant Setup - Security" page, scroll down to the "Multi-Factor Authentication Providers" table and click the Add Multi-Factor Authentication ... button.
-
On the "Add Multi-Factor Authentication Provider" page, select Duo from the "Provider Type" options and click OK.
-
Click the Edit button next to the Duo provider.
-
On the next page, check the box next to Enabled and enter the Duo Workday and Admin API application information from the Duo Admin Panel as follows.
Auth Integration Key The integration key (i.e. DIXXXXXXXXXXXXXXXXXX) from your Workday application.Auth Secret Key The secret key from your Workday application. Admin Integration Key The integration key (i.e. DIXXXXXXXXXXXXXXXXXX) from the Admin API application you created to use with Workday.Admin Secret Key The secret key from the Admin API application you created to use with Workday. API Hostname Your API hostname (i.e. api-XXXXXXXX.duosecurity.com).Username Format Select the name format used when sending the Workday username to Duo. One of Email Address or Username. 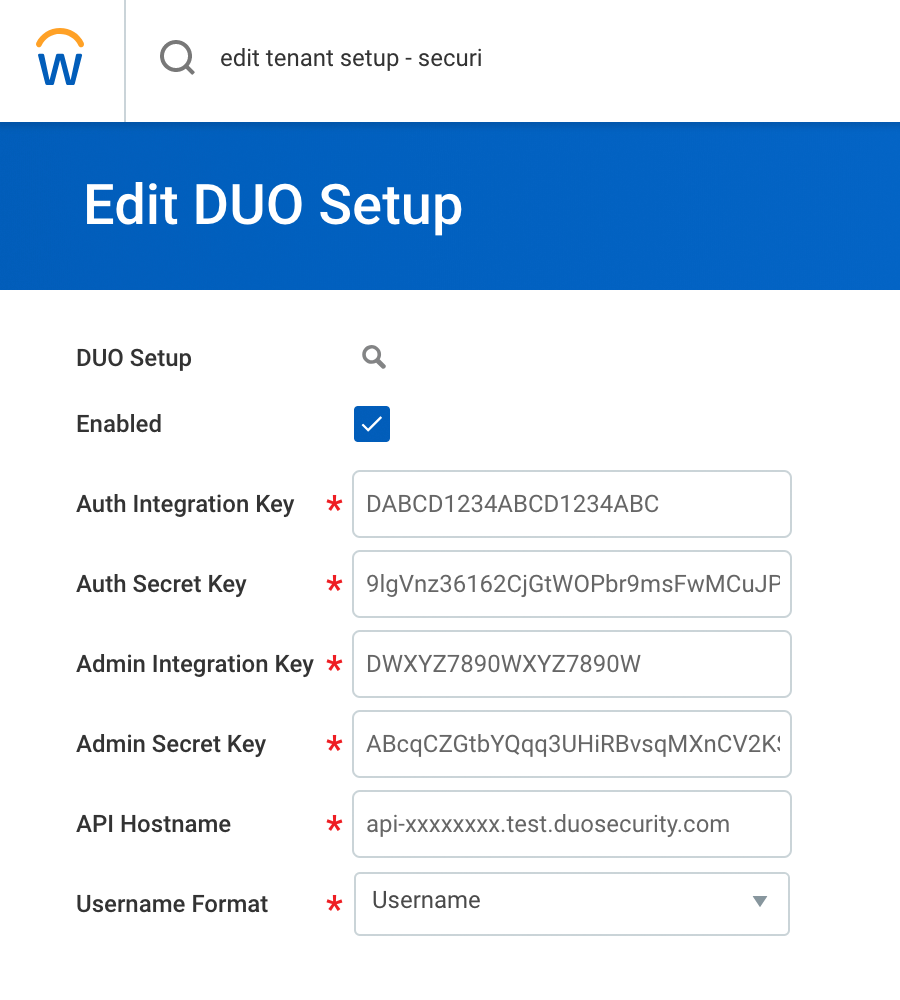
-
Click OK to save your changes.
Refer to Steps: Set Up Multi-Factor Authentication Using Duo Security and Reference: Edit Tenant Setup - Security: Multi-Factor Authentication Providers in the Workday documentation for more information.
Add Duo to an Authentication Policy
- While logged into Workday as an administrator, access the Manage Authentication Policies report.
- Choose whether you will edit an existing authentication policy to add Duo, or create a new one. Note that an authentication rule that includes Duo as the multifactor authentication type should also have User Name Password as the authentication type.
- Edit the authentication policy so that the authentication ruleset includes the Duo multifactor authentication provider you created earlier as the Multi-factor Authentication condition.
- Save the changes to your authentication policy, and then activate your policy changes.
Here is an example authentication policy ruleset that includes a rule called "Duo MFA" which applies the Duo MFA condition to members of a "Duo MFA Users" user-based security group.
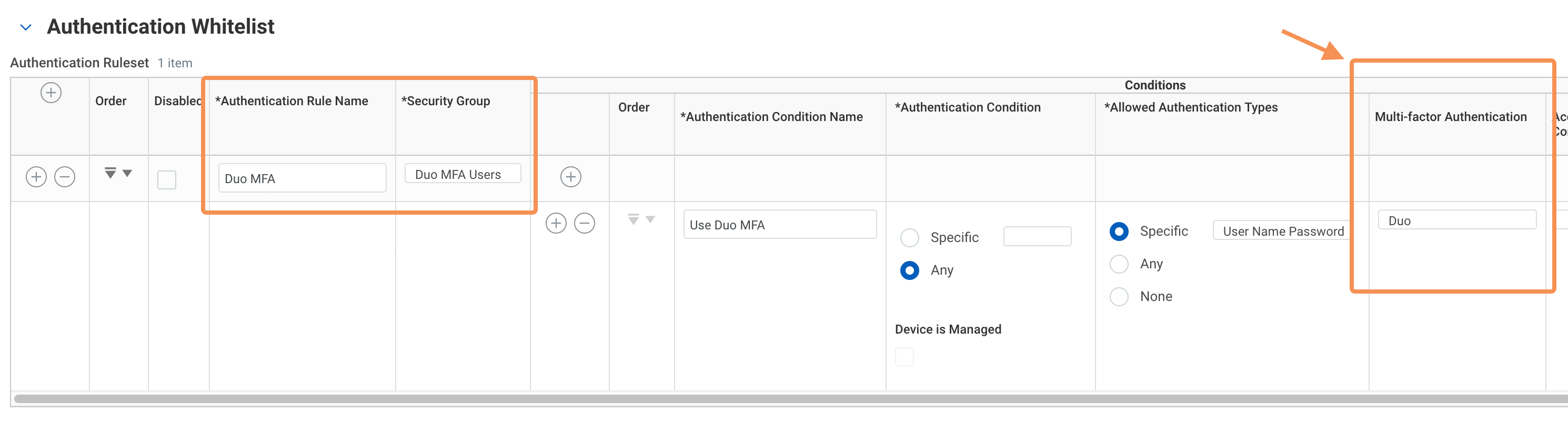
Please refer to Add Authentication Rules in the Workday documentation for detailed information and guidance for creating your own authentication policies and rulesets that include Duo MFA.
Test Your Setup
Duo Enrollment
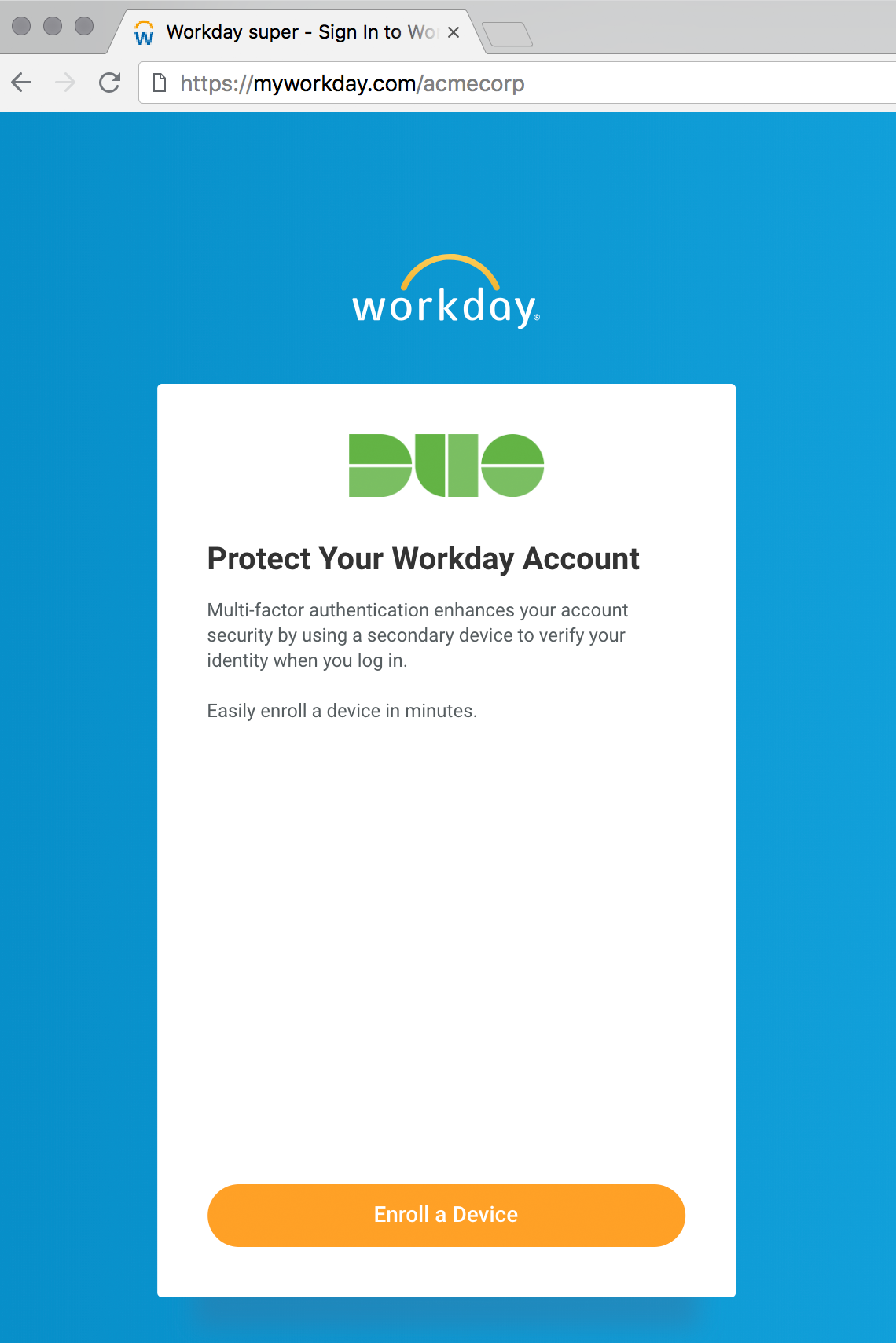
When a Workday user logs in using your new Duo MFA authentication policy, Workday check to see if this user already exists in Duo with valid authentication factors. If the user doesn't exist, then they'll begin the enrollment process. Users can add a a landline for phone call verification, or a mobile phone or tablet activated for Duo Push notifications for two-factor authentication approval.
Duo Authentication
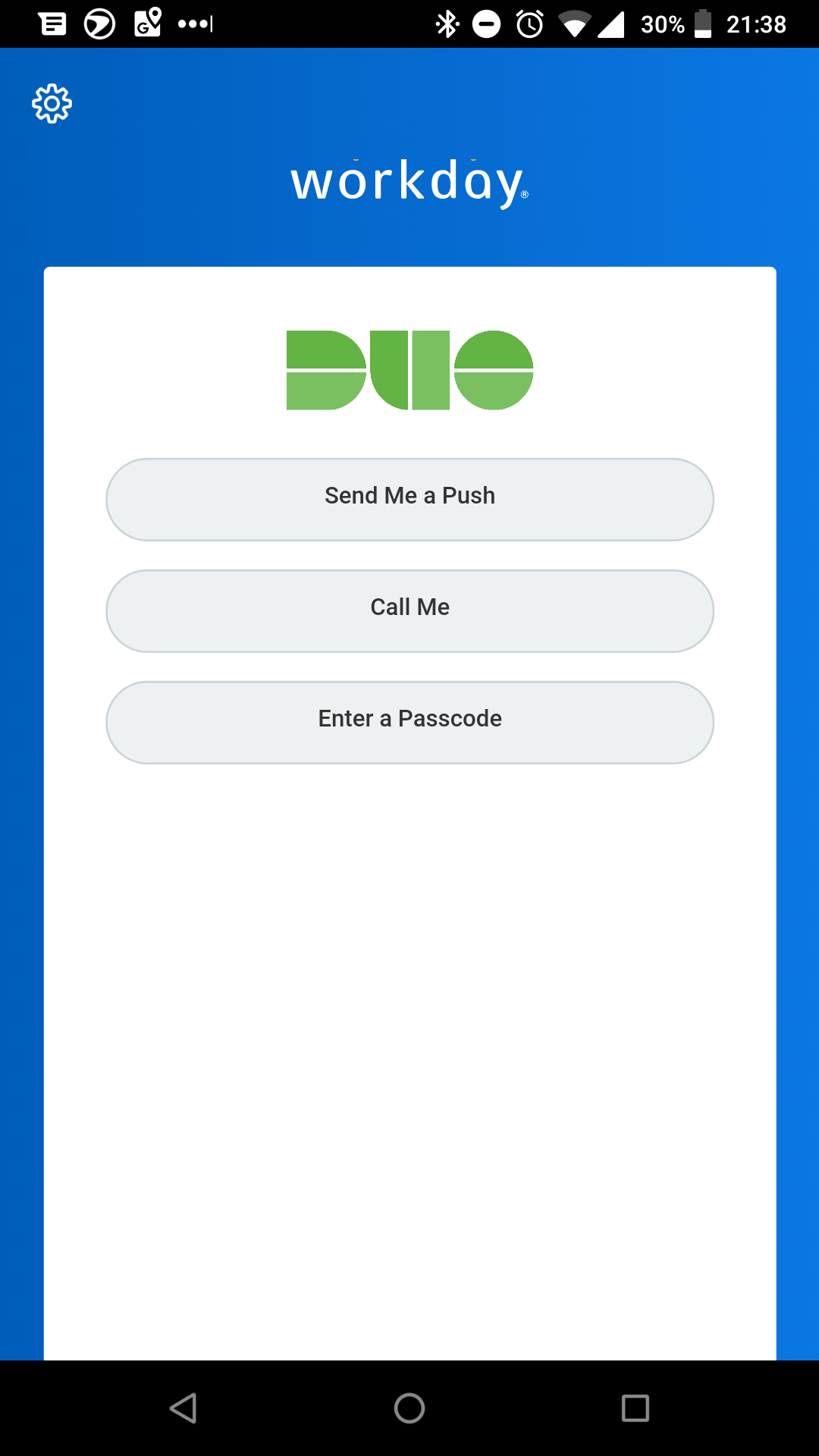
Once enrolled, Workday users see a prompt for Duo authentication. Choose from one of the available authentication methods.
| Method | Description |
|---|---|
| Send Me a Push | Pushes a login request to a phone or tablet (if Duo Mobile is installed and activated on an iOS, Android, or Windows Phone device). Review the request and tap Approve to log in. |
| Call Me | Authenticate via phone callback to a mobile phone or landline. |
| Enter a Passcode | Log in using a passcode, either generated with Duo Mobile, sent via SMS, generated by a hardware token, or provided by an administrator. Click Text me new codes to send a new batch of passcodes to a mobile phone via text message. |

Duo MFA and Workday Mobile App
The Workday mobile app also supports Duo enrollment and authentication.
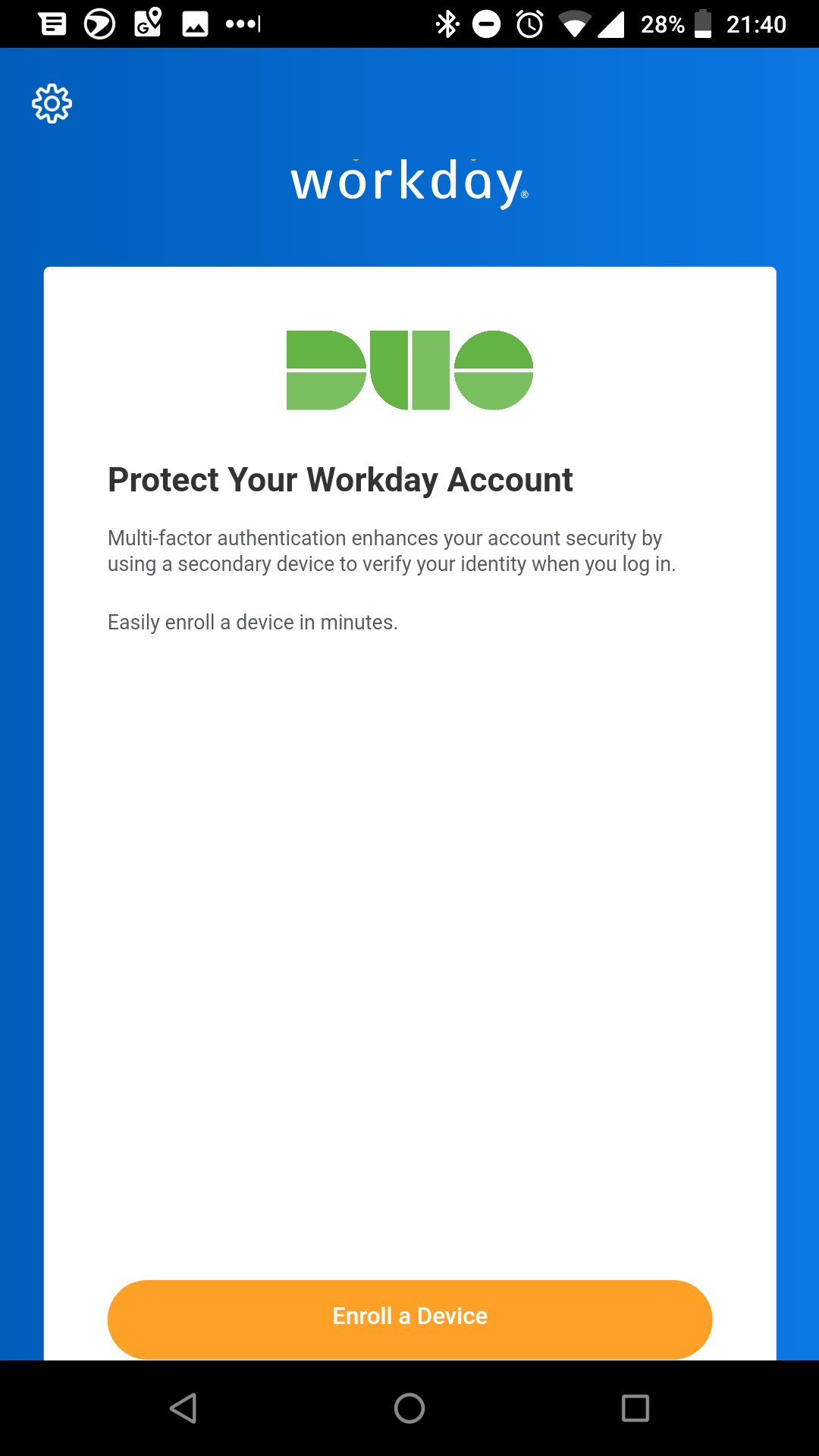
Duo Enrollment in Workday Mobile App
Duo Authentication in Workday Mobile App
Additional Operations
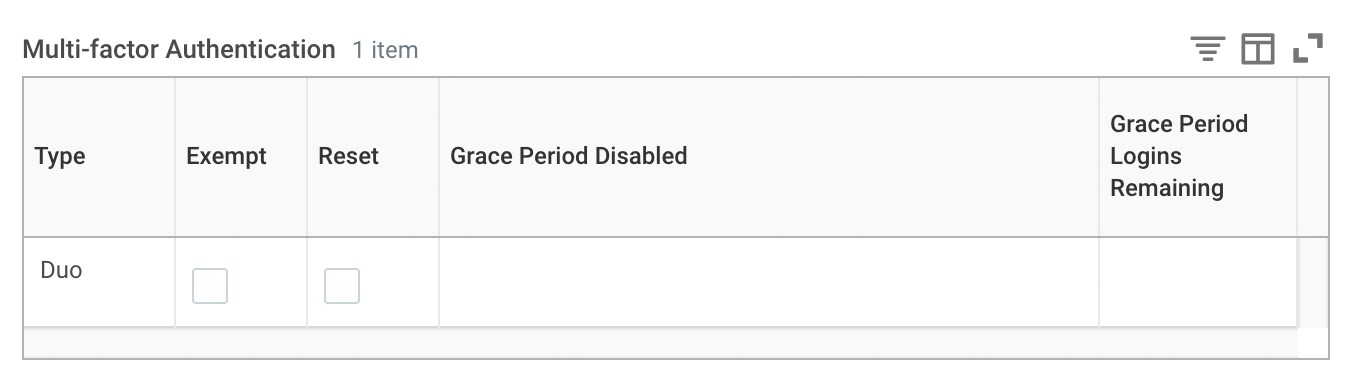
Changing Duo MFA Options for Users
You can exempt individual Workday users from the MFA requirement or reset a user's MFA status. Access the Edit Workday Account action and locate the user, then scroll down to the "Multi-Factor Authentication" section of the page.
Viewing Signon Activity
Access the Signons and Attempted Signons report to review authentication activity. The Requires MFA and Multi-factor columns indicate if the user was required to log in with multifactor authentication and the name of the MFA provider used (e.g. Duo).
Known Issues
-
A user with only a hardware token assigned as the sole authentication method may not log in, and will receive an error from Workday. Assign a mobile phone to the user and they can then complete authentication with a token passcode.
-
A user with Duo Bypass status assigned or one who would not require Duo MFA at login due to the Allow access without 2FA Duo New User Policy setting or Bypass 2FA Duo Authentication Policy setting applied to the Workday application may not log in when subject to a Workday authentication rule that includes Duo MFA. Exempt these users from Duo authentication from within Workday, either via the Authentication Policies rulesets or individually per user by editing their Workday account.
-
The Workday authentication prompt respects authentication method policy restrictions, but the enrollment process does not. To avoid a scenario where users enroll devices that may not then be used to authenticate due to policy restrictions, consider using another Duo enrollment method, like bulk enrollment or directory sync.
-
Policy settings based on user IP address, such as User Location, Authorized Networks, or Anonymous Networks, do not apply to the Workday application. These policies do apply to Workday SSO configurations.
Troubleshooting
Need some help? Try searching our Knowledge Base articles or Community discussions. For further assistance, contact Support.
