Documentation
Duo Two-Factor Authentication for Microsoft Entra ID External Authentication Methods (EAM)
Last Updated: September 19th, 2024Contents
Duo integrates with Microsoft Entra ID as an external authentication method to add two-factor authentication to Entra ID logons, offering inline user enrollment, self-service device management, and support for a variety of authentication methods — such as passkeys and security keys, Duo Push, or Verified Duo Push — in the Universal Prompt.
About Microsoft EAM
Microsoft opened up the Azure Active Directory (now known as Entra ID) ecosystem in 2017 to allow third-parties, like Duo, to create custom controls for additional authentication. The Duo custom control for conditional access lets users log in with the simple and feature-rich Duo two-factor authentication prompt, but not without some platform limitations — most significant among them that additional authentication completed within a custom control does not satisfy conditional access policies that require multifactor authentication (MFA).
In 2020, Microsoft announced their intent to replace custom controls with a new method of integrating third-party authentication. As a trusted partner, Duo has been collaborating with Microsoft to deliver an authentication solution for their new Microsoft External Authentication Methods, or EAM framework, available as of May 2024.
Duo is among the first third-party providers delivering an integration on this new platform, and Duo via EAM is fully-recognized as a multifactor authentication method in Entra ID, satisfying MFA policy requirements. Once you define Duo as an EAM provider, you will be able to create Entra ID conditional access policies with MFA via Duo and assign them to specific users, groups, or applications.
Learn more about the EAM public preview on the Microsoft blog.
Known Limitations
-
Users who are able to bypass Duo MFA — because the user has "Bypass" status applied directly or via Duo group membership, or the user's effective policy for the Entra ID EAM application in Duo has the new user policy set to "Allow access without 2FA", the authentication policy set to "Bypass MFA", or the policy has an authorized networks configuration that does not require 2FA — may not use Duo as an external authentication method for Entra ID MFA. These users will receive an error in the Microsoft portal and be unable to complete authentication.
The claim returned to Microsoft after Duo authentication includes information about the factor used to satisfy MFA requirements. When a user bypasses active Duo authentication the MFA factor requirement is not satisfied during this authentication. To avoid these failures, adjust your Duo policies or effective status of your users so they can satisfy the MFA requirement, or adjust your Entra ID conditional access policy so that it does not target users who are able to bypass Duo authentication.
Bypassing Duo authentication via a valid remembered devices session is supported and returns a valid MFA method for external authentication.
-
Users must explicitly choose the Duo EAM option during authentication. If they have other MFA methods besides Duo configured, they may need to click Other options on the Microsoft "Verify your identity" prompt to be able to choose the Duo method. Microsoft plans to add system-preferred defaults for EAM in the future, which will prioritize the default method displayed during authentication.
-
The Duo external authentication method doesn't support external guest user logins.
-
The Duo external authentication method does not fully support cross-tenant users. Cross-tenant user authentication will only work if:
- The external Microsoft Entra organization trusts MFA claims from the authenticating user’s home tenant.
- The authenticating user has a valid MFA claim established via authentication to an application in their home tenant before accessing the cross-tenant application.
-
Azure Government does not yet support Entra ID external authentication methods. Be sure to review Microsoft Entra feature availability in Azure Government.
- Due to EAM feature unavailability in Azure Government, the "Microsoft Entra ID: External Authentication Methods" application is not available in Duo Federal plans.
Prerequisites
-
An active Entra ID P1 or P2 subscription including Conditional Access, with the P1/P2 licenses assigned to each user that will log in using Duo MFA. Microsoft 365 E3, E5, and F3 plans, Enterprise Mobility + Security E3 and E5 plans, and Microsoft Business Premium include Entra ID Premium.
-
A designated Entra ID admin service account to use for authorizing the Duo application access. This account needs the Entra ID Global Administrator or Privileged Role Administrator role during Duo setup, but you can reduce the service account's role privileges later. This service account may or may not require Entra ID MFA for admins at login (learn more about the baseline MFA policy for Entra ID admins).
Create the Duo Entra ID Application
Before starting these steps, you should either not be logged in to the Microsoft Entra admin center at all, or be logged in as the designated service account with the necessary role privileges for Duo you created as a prerequisite.
-
Sign up for a Duo account if you do not already have one.
-
Log in to the Duo Admin Panel and navigate to Applications.
-
Click Protect an Application and locate Microsoft Entra ID: External Authentication Methods in the applications list. Click Protect. See Protecting Applications for more information about protecting applications in Duo and additional application options.
-
Before you can proceed, Duo needs read access to your Entra ID tenant. Click the Authorize button, which takes you to the Microsoft portal.
-
Sign in with the designated Entra ID service administrator account. If required, complete Entra ID MFA for that service account admin user.
Duo does not see or store your Entra ID administrator credentials.
-
Once you've signed in to Entra ID, you must check the box next to Consent on behalf of your organization and then click Accept to grant the Cisco Duo External Authentication Method application the rights needed to access and read directory information from your Entra ID tenant.
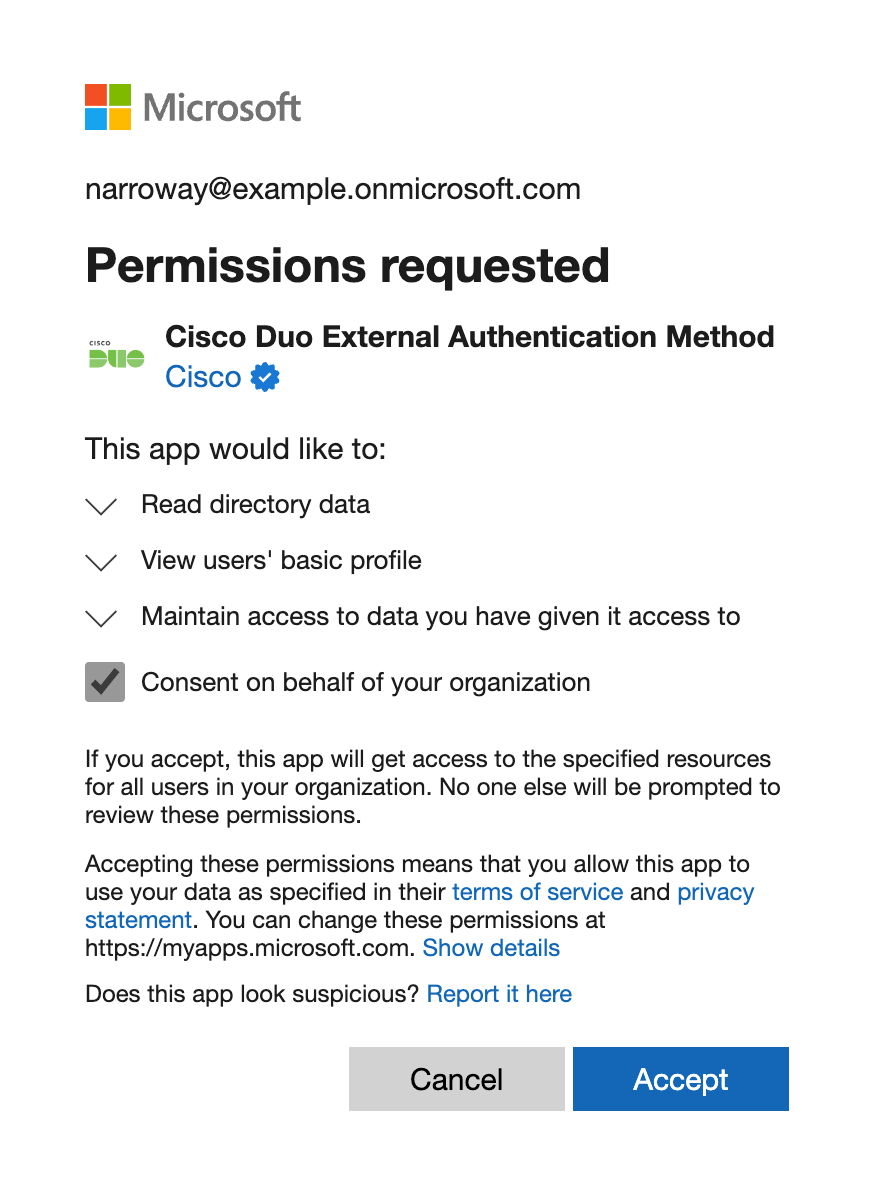
-
Accepting the Duo Entra ID Authentication application's permissions request redirects you back to the Microsoft Entra ID: External Authentication Methods application page in the Duo Admin Panel.
-
You can adjust additional settings for your new Microsoft Entra ID: External Authentication Methods application Duo application at this time — like changing the application's name from the default value, enabling self-service, or assigning a group policy — or come back and change the application's policies and settings after you finish Entra ID setup (note that the "Hostname Whitelisting" settings have no effect on this application). If you do update any settings, click the Save Changes button when done.
-
Keep the Duo Admin Panel open so you can copy Duo application information into the Entra ID admin center in the next steps.
Duo Universal Prompt
The Duo Universal Prompt provides a simplified and accessible Duo login experience for web-based applications, offering a redesigned visual interface with security and usability enhancements.
| Universal Prompt | Traditional Prompt |
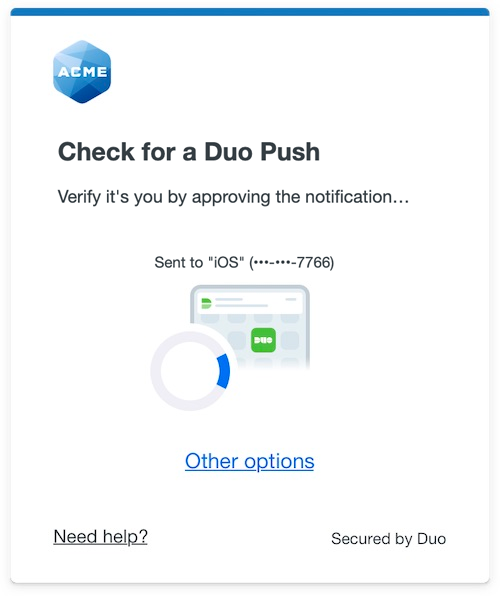 |
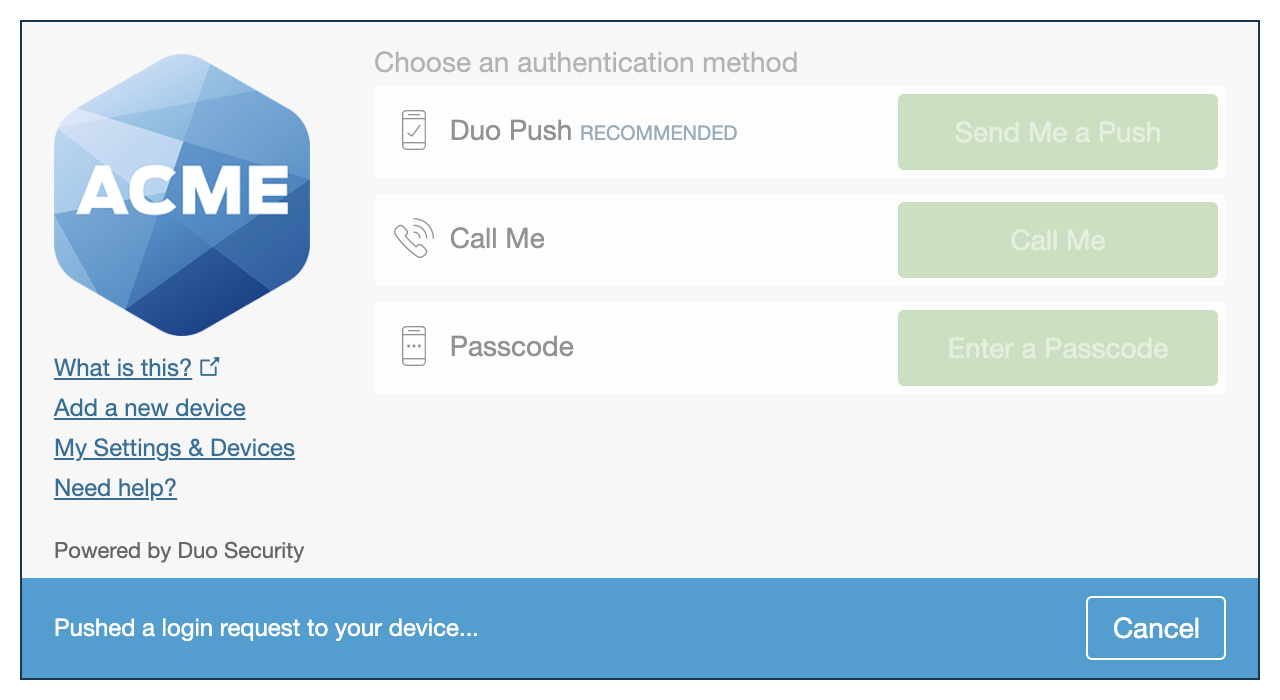 |
The Duo Microsoft Entra ID: External Authentication Methods application supports the Universal Prompt by default, so there's no additional action required on your part to start using the newest authentication experience.
Activate Universal Prompt
Activation of the Universal Prompt is a per-application change. Activating it for one application does not change the login experience for your other Duo applications. Universal Prompt is already activated for new Microsoft Entra ID: External Authentication Methods applications at creation.
The "Universal Prompt" area of the application details page shows that this application's status is "Activation complete", with these activation control options:
- Show traditional prompt: Your users experience Duo's traditional prompt via redirect when logging in to this application.
- Show new Universal Prompt: (Default) Your users experience the Universal Prompt via redirect when logging in to this application.
The application's Universal Prompt status shows "Activation complete" both here and on the Universal Prompt Update Progress report.
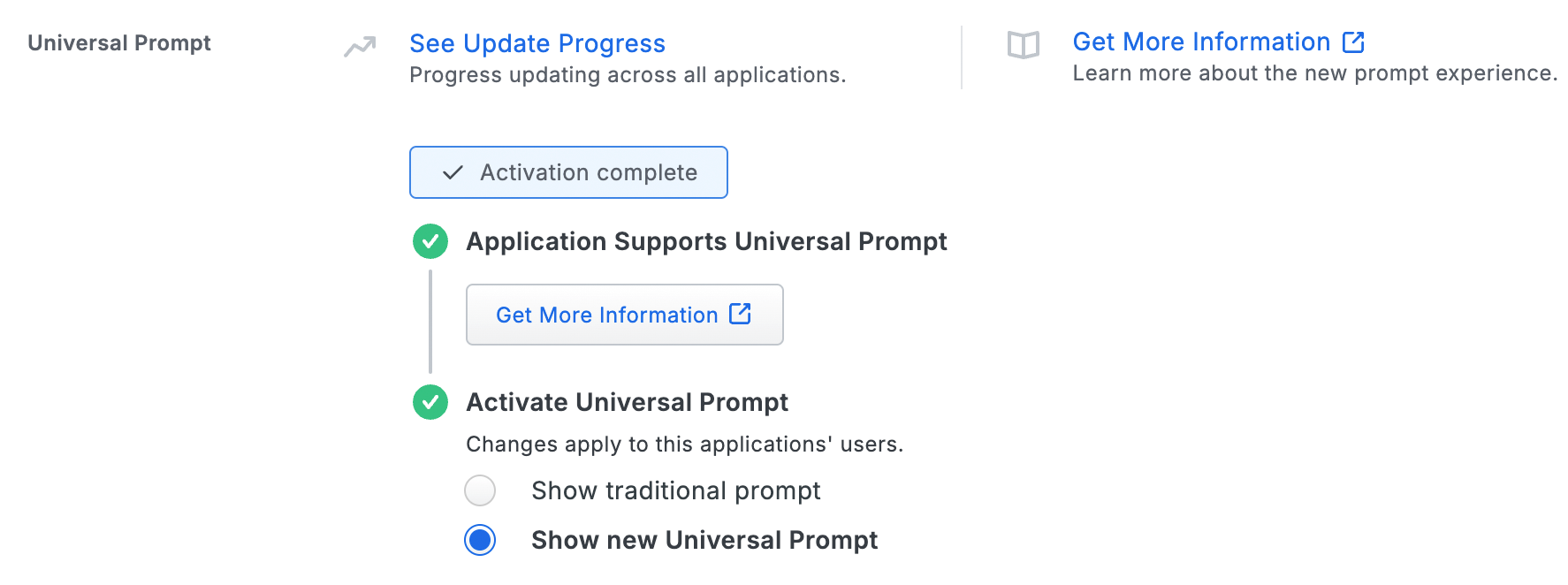
For the time being, you may change this setting to Show traditional prompt to use the legacy experience. Keep in mind that support for the traditional Duo prompt ended for the majority of applications in March 2024. This option will be removed in the future.
Universal Update Progress
Click the See Update Progress link to view the Universal Prompt Update Progress report. This report shows the update availability and migration progress for all your Duo applications. You can also activate the new prompt experience for multiple supported applications from the report page instead of visiting the individual details pages for each application.
Configure Entra ID
Create the Duo MFA External Authentication Method
-
Log in to your Entra ID tenant in the Microsoft Entra admin center at https://entra.microsoft.com as a global administrator (if you aren't already logged in).
If you try to perform these configuration steps from the Azure portal (https://portal.azure.com) the navigation is slightly different.
-
In the Entra Admin Center, go to Protection → Authentication Methods → Policies.
If you logged into the Azure portal instead of the Entra Admin Center, first click Microsoft Entra ID then go to Security → Authentication Methods → Policies.
-
Click + Add External Method.
-
Once on the "Add external method" page enter a descriptive Name for the Duo Method. We have provided the default name "Cisco Duo" but you may enter a different name. Your users see this name during Entra ID authentication as they choose which authentication method to use, so use a name that makes sense to users in your organization. You can't change the name after creation.
-
Return to the Duo Admin Panel and copy the Client ID value from the Microsoft Entra ID: External Authentication Methods application's page. Switch back to the Entra ID admin center and paste it into the Client ID field on the "Add external method" page.
-
Copy the Discovery Endpoint value from the Microsoft Entra ID: External Authentication Methods application's page in the Duo Admin Panel, and then paste it into the Discovery Endpoint field in Entra ID.
-
Copy the App ID value from Duo for the application, and paste it into the Entra ID App ID field.
-
If you want to enable the new Duo EAM method immediately, toggle Enable from Off to On.
-
Before saving the new Duo external method, choose which users you want to use this new method. By default, it applies to all users, meaning that any Entra ID user in your tenant with an effective Conditional Policy set to "Require multifactor authentication" will see Duo as an authentication option as soon as you enable this new method.
If you wish to target availability of the Duo external method to specific users, click + Add Target on the "Include" tab and choose Select Targets. On the "Add directory members" page you can select one or more of your Entra ID directory groups containing the users you want to use Duo authentication. Click Select to add your choices as targeted groups.
-
After entering all required information click Save to create the new Duo external method.
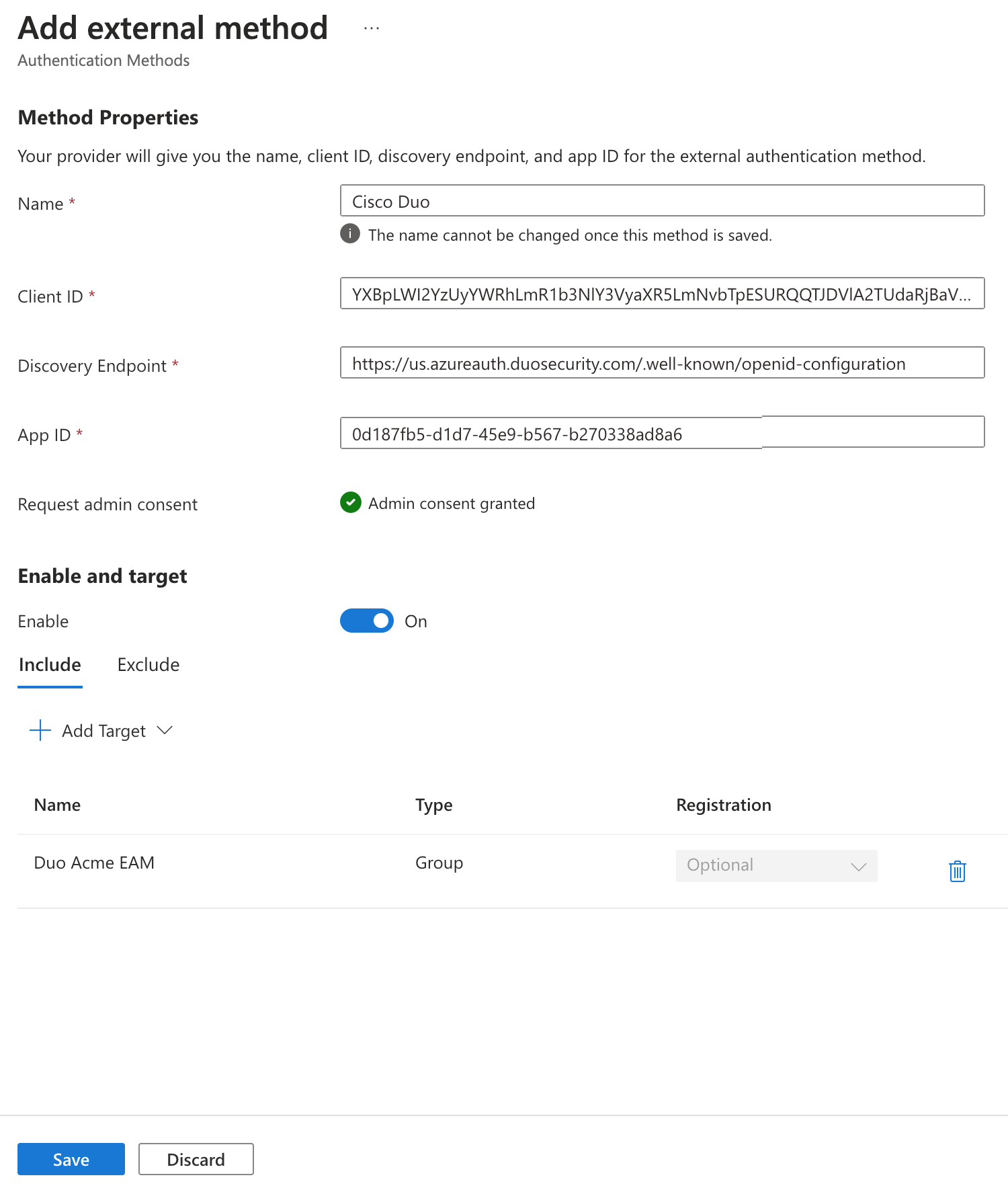
Note: If the "Request admin consent" information shows a Request permission button instead of saying "Admin consent granted", double-check to make sure you entered the correct App ID value from the Duo Admin Panel. If the App ID information is correct, click the Request permission button to authorize the grant the Cisco Duo External Authentication Method application, making sure to check the box next to Consent on behalf of your organization before clicking Accept.
Create and Apply a Duo Conditional Access Policy
-
While still in the Microsoft Entra admin center click Conditional Access on the left and then click + Create New Policy.
If you are in the Azure portal, go to Security → Conditional Access → Policies.
-
Enter a descriptive name for the new policy, for example "Duo MFA for Acme Users".
-
Make your desired policy assignments. You can assign this new policy to selected users or Entra ID security groups, to specific Entra ID cloud apps, or to any of the other Entra ID conditions like client platform or network.
-
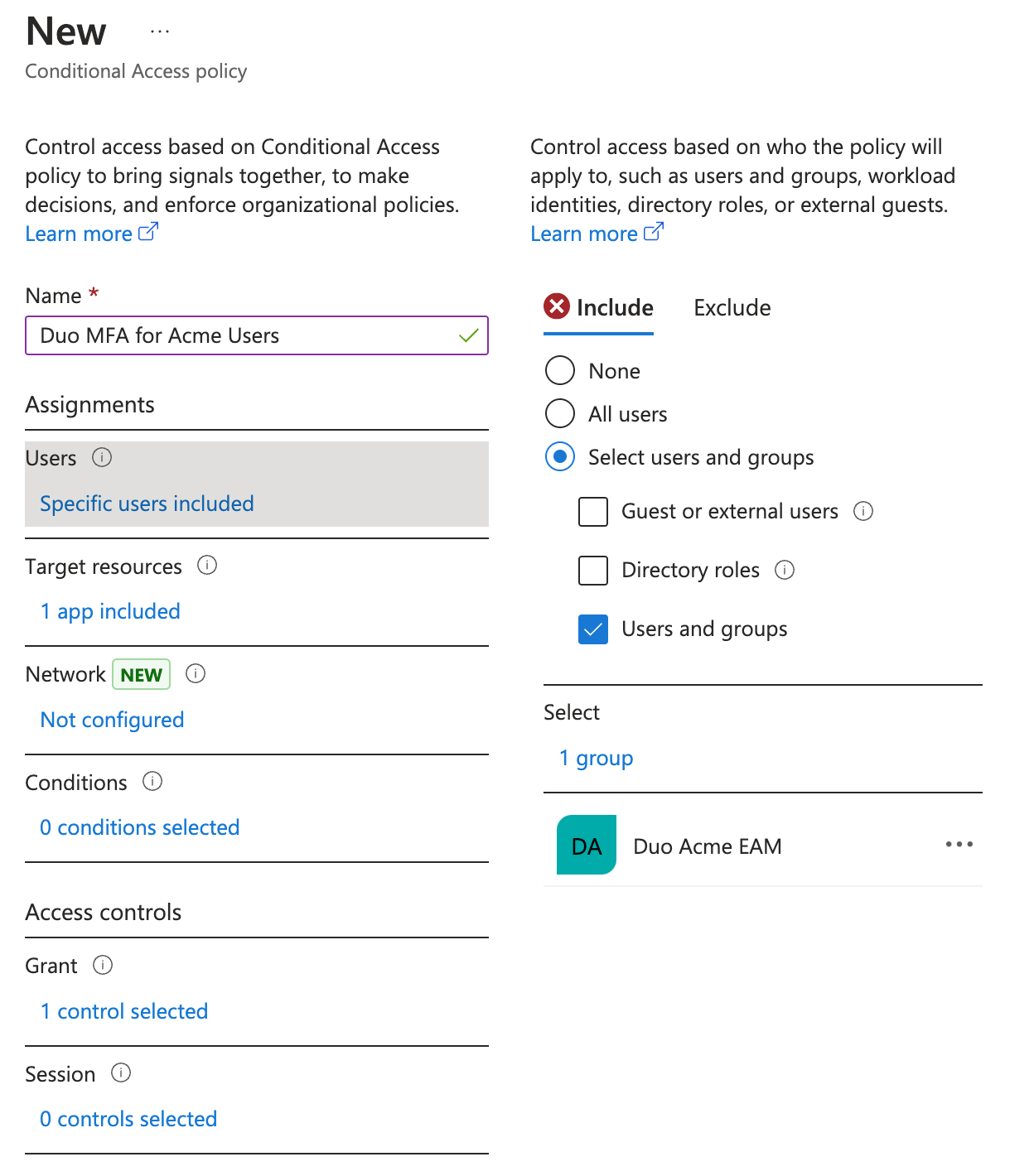
As an example, click on Users under "Assignments", click Select users and groups on the "Include" tab, choose Users and groups, click 0 users and groups selected. and locate the users or Entra ID security groups you want to authenticate with Duo. Click on a user or security group to select it, then click the Select button on the "Select users and groups" page to apply your selection. If you targeted specific groups when creating your Duo external method then make sure to apply the new policy to those same groups.
In this example the new Duo policy assignment includes the Entra ID group "Duo Acme EAM", so members of that group will see Duo as an available authentication method when logging in to Entra ID.
-
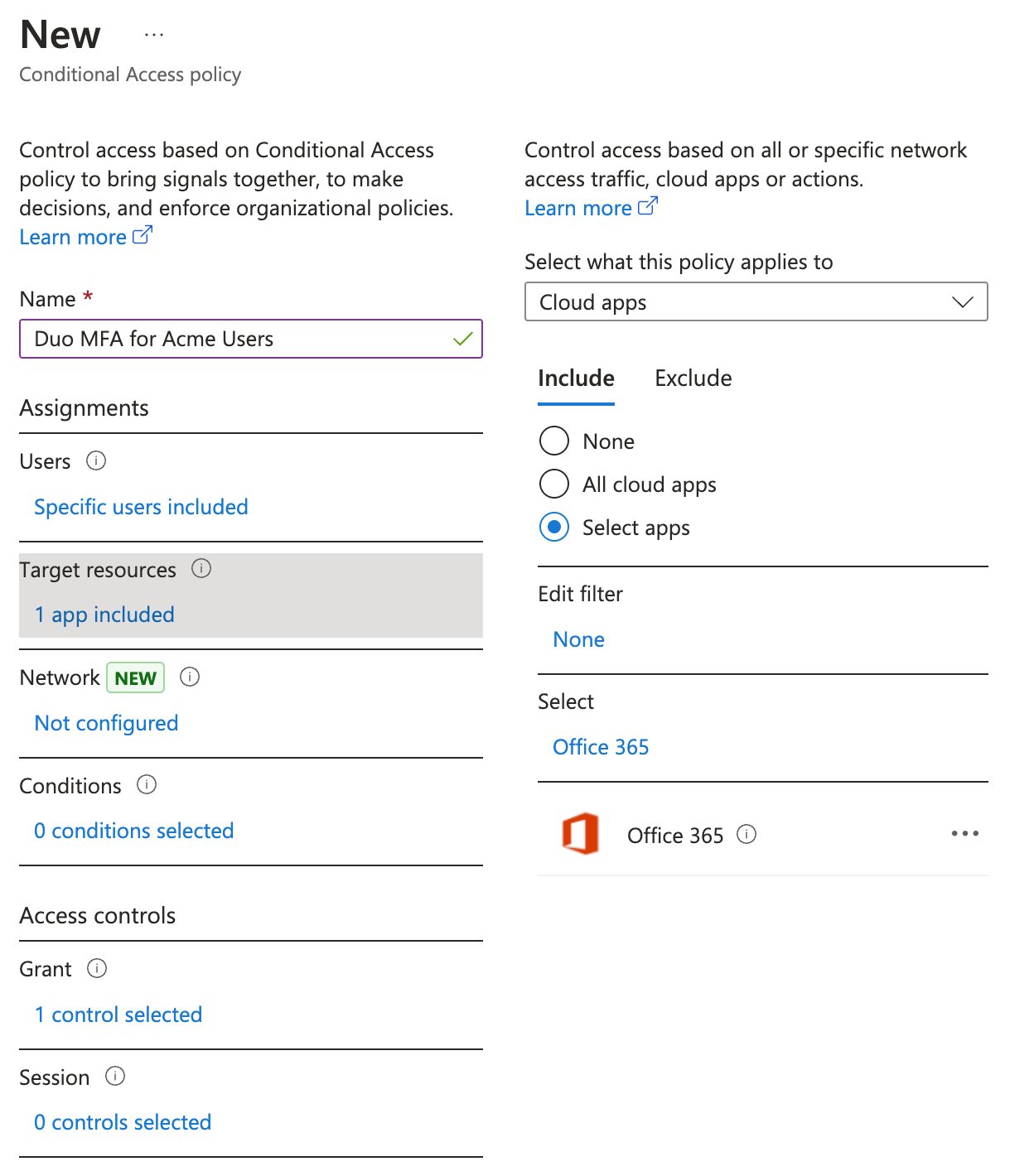
Next, click on Target resources. On the "Include" tab, click Select apps and choose the Entra ID applications where you want Duo authentication before access.
In this example the Duo cloud apps assignment applies to "Office 365". Other Entra ID applications not specified by the policy assignment will not apply this conditional access policy at login and therefore will not offer the Duo MFA method.
Note: We don't recommend assigning the Duo policy to all users (including tenant administrators) or to all cloud apps at first to avoid the risk of inadvertently blocking administrator access to the Entra ID portal. Verify that your Duo policy and EAM factor work properly before assigning the policy to your tenant administrators or to all cloud apps. You should create a fail-safe Entra ID tenant administrator account that is excluded from Duo MFA policies to ensure uninterrupted admin access. Apply a secure password and a different access condition, like one based on a trusted network, to secure this admin account.
-
Make any additional policy assignments you wish, such as defining networks or conditions.
-
-
Click Grant under "Access controls", and then click on Grant access and check the box for Require multifactor authentication. Click Select when done.
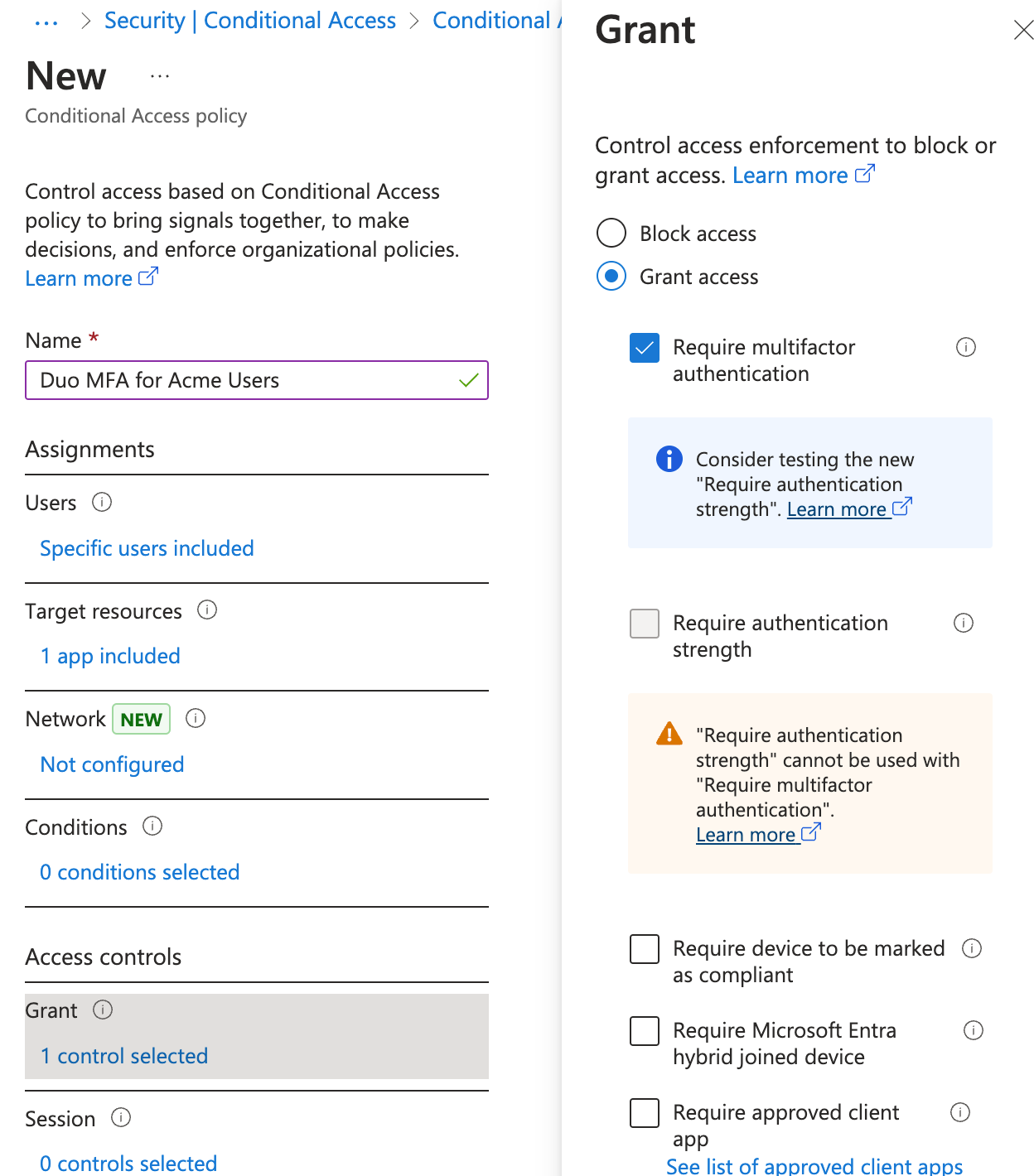
-
The final step to creating the new Duo policy is to enable it. Click the On toggle switch underneath "Enable policy", and then click Create. Entra ID creates and enables the new MFA-required policy targeting your selected groups or users.
You may want to prevent Entra ID from offering your users the option to set up the Microsoft Authenticator app for sign-in if you will want them to use Duo instead.
-
In the Entra ID admin center go to Protection → Authentication methods → Registration campaign.
-
Click Edit and change the State to Disabled. Click Save. You could also leave the registration campaign on and exclude any groups of users to which you applied the Duo MFA conditional access policy instead.
-
Go to Protection → Authentication methods → Settings → System preferred multifactor authentication.
-
Click Edit and change the State to Disabled. Click Save.
-
Go to Protection → Policies. Click Microsoft Authenticator.
-
On the “Enable and Target” tab, click the Enable toggle to turn Microsoft Authenticator Off. Click Save.
Test Your Setup
Log in to Entra ID as a user assigned the CA policy which reqires MFA and who is a target of the newly-created Duo external method.
If you chose to apply the Duo Conditional Access policy to "All cloud apps", then when you log into the Office portal and submit your primary Entra ID credentials, you'll see your Duo external authentication method as an option for identity verification. The name shown here is the name you entered when you created the Duo external method in Entra ID.
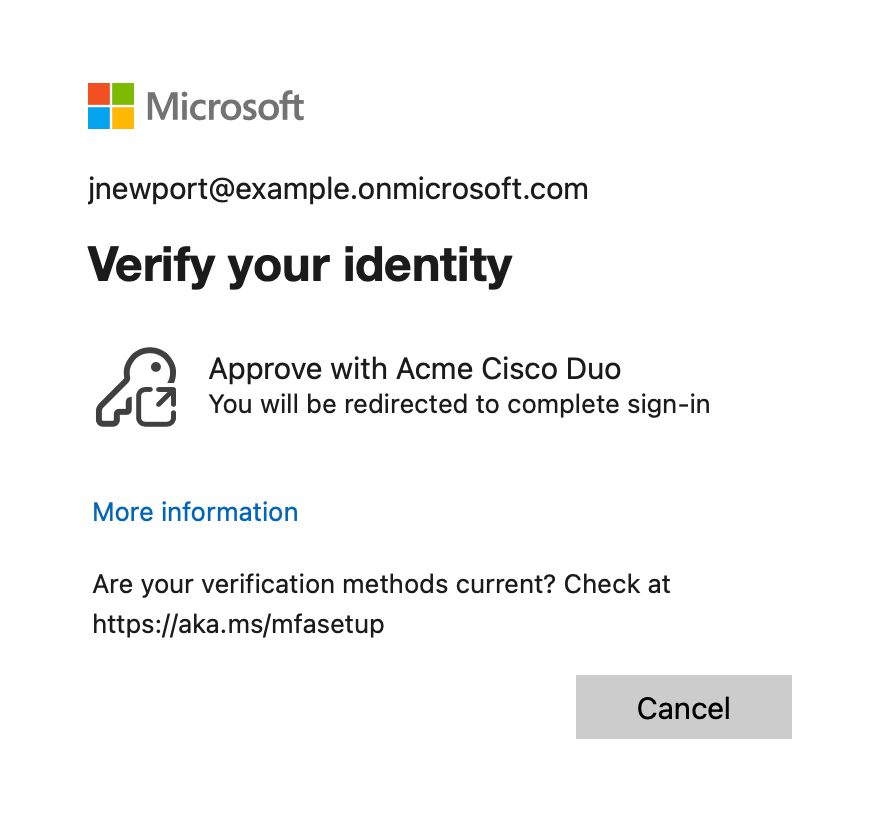
Select the Duo MFA EAM method to begin Duo authentication. If you have multiple Entra ID authentication methods enabled you may need to click Other options to see the Duo authentication method.
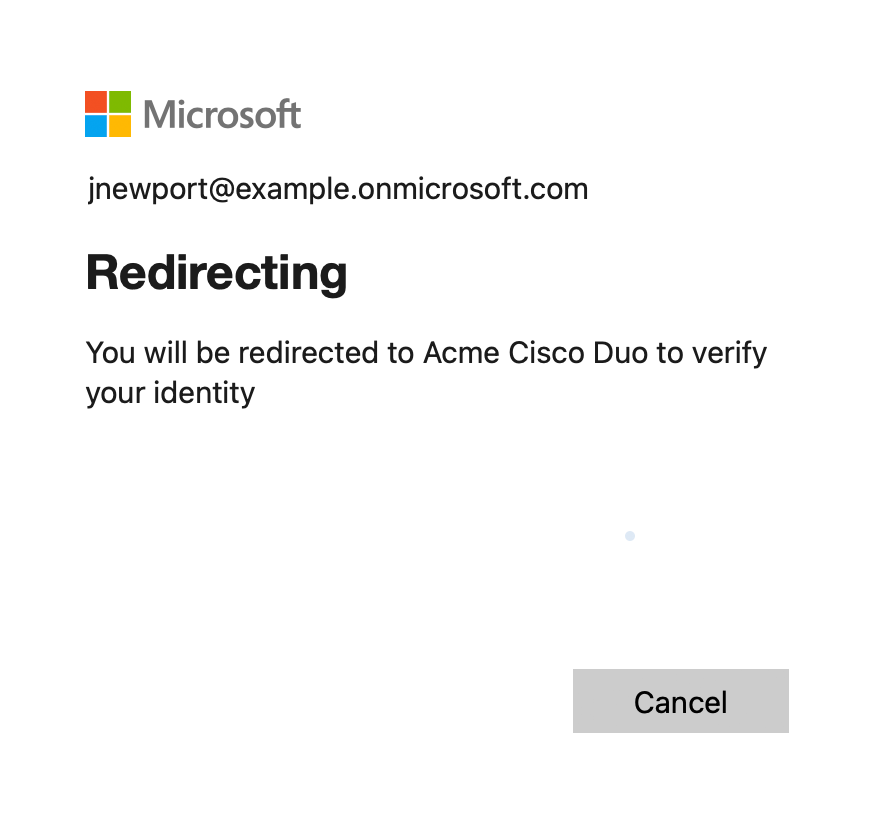
You'll be redirected to the Duo Prompt or Duo user enrollment. Completing Duo authentication returns you to Entra ID to complete your application login.
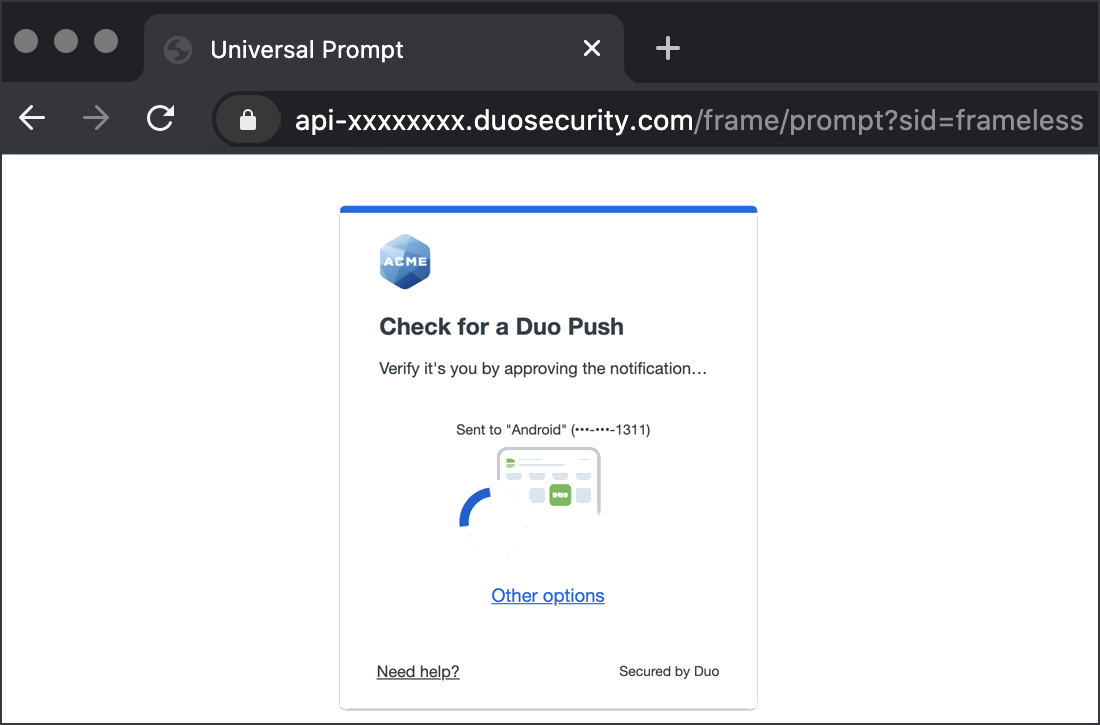
*Universal Prompt experience shown.
If you applied the conditional access policy requiring MFA to specific applications, then the initial Office portal login won't prompt for Duo MFA, but accessing the protected application from within the Office portal after logging in or accessing the protected application directly (bypassing the Office portal) will prompt for Duo MFA.
If you receive a "Looks like something went wrong" error message from Microsoft, it could be that the new EAM settings need a few more minutes to take effect. If the error persists, check the Duo Admin Panel to make sure that the test user isn't bypassing Duo authentication, as mentioned in the known limitations for the Duo external method.
Migration from the Duo Custom Control to Duo External Authentication Method
If you've already applied conditional access policies requiring the Duo custom control for Entra ID before granting application access, you can migrate your users to use Duo as an external authentication method without interrupting secured access to your applications. You can configure Duo EAM in parallel with the Duo CA custom control and switch users from one to the other by adjusting their effective conditional access policies.
An example migration could look like this:
- Survey your user groups to determine which ones contain your EAM pilot users.
- Create the Duo EAM external method, targeting your pilot group or groups.
- Create a new conditional access policy for multifactor via Duo EAM.
- Apply the Duo EAM conditional access policy to your pilot user groups.
- Remove the conditional access policy which requires the Duo custom control from your pilot user groups.
- Have your pilot users test Duo as an external authentication method.
- After receiving positive feedback from your initial pilot users, gradually expand testing to include more user groups by updating the Duo EAM method's target groups and the Duo EAM group policy assignments to add additional user groups, while also removing those additional groups from your Duo custom control CA policies.
- When you're ready to stop using the Duo custom control, change the Duo EAM target group to "All Users", apply CA policies requiring MFA to all your users, and remove all group and user assignments from your Duo custom control CA policies.
- Delete the Duo custom control from Entra ID.
If any Entra ID user is subject to conditional access policies that require use of the Duo custom control for conditional access, while also being subject to CA policies which require multifactor authentication after the Duo external method is added, and the user is in a group targeted by the Duo external method, then that user will have to perform Duo authentication twice — once using EAM and once via the custom control — to satisfy both CA policies before gaining access to applications.
Troubleshooting
Need some help? Take a look at our Microsoft Azure Active Directory or Entra ID Knowledge Base articles or Community discussions. For further assistance, contact Support.
Network Diagram
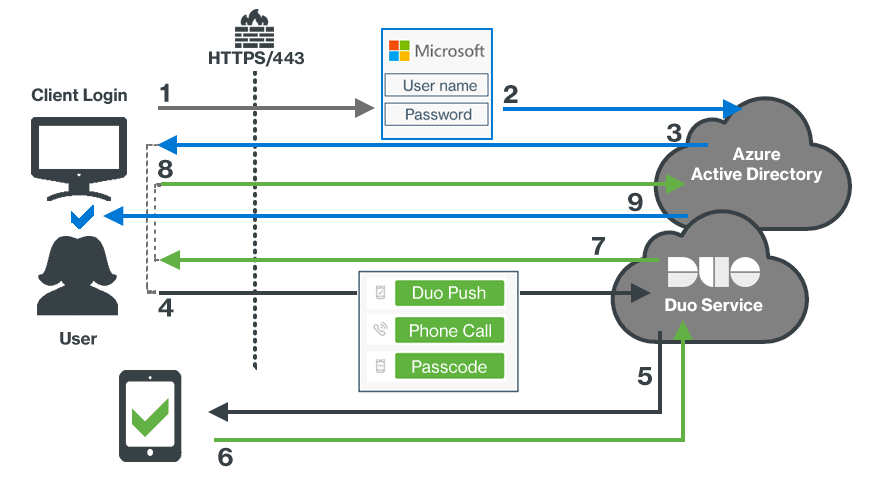
- User accesses Microsoft Online or other services using Entra ID authentication.
- User submits primary Entra ID credentials.
- User selects the Duo EAM method, which redirects the client browser to Duo.
- User receives the Duo Prompt and submits factor selection.
- User receives Duo Push authentication request on device.
- Authentication approval returned to Duo service.
- Secondary authentication approval returned to client.
- Client sends Duo approval back to Entra ID.
- Entra ID grants application or service access once the MFA requirement and all other aspects of the user's effective conditional access policy is satisfied.
